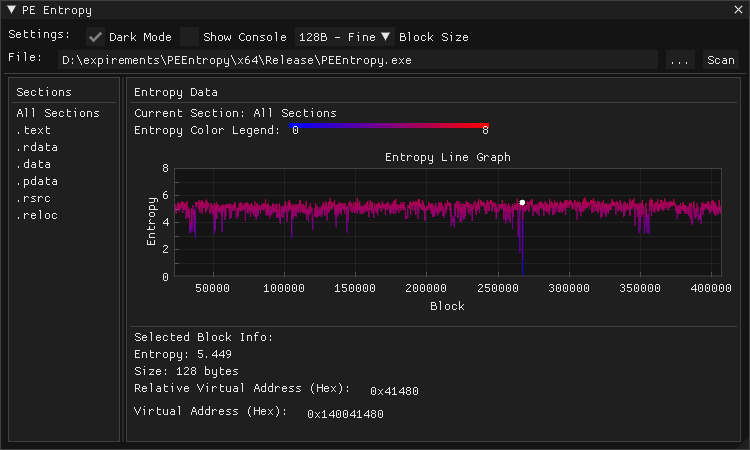
A PE file entropy visualization tool for Windows, designed for malware analysts, reverse engineers, and anyone who wants an intuitive look at entropy patterns in binaries.
Built using ImGui with the DirectX 11 backend.
- PE section scanning – automatically detects and lists all sections.
- Per-block entropy analysis – configurable block sizes for fine → coarse inspection.
- All-sections mode – visualize entropy across the entire binary in a single graph.
- Interactive entropy graph
- Hover blocks to inspect RVA, VA, entropy, and size
- Click blocks to lock selection
- Copy-paste ready addresses
- Displays IDA/Ghidra-ready RVA and VA
- One-click selection → paste → jump to code/data instantly
- Dark / Light theme toggle
- Optional console output for debugging and scan logs
- If the program fails to launch, install the Microsoft Visual C++ Redistributable (x64): https://learn.microsoft.com/en-us/cpp/windows/latest-supported-vc-redist
Entropy alone is not useful unless you can act on it.
This tool is designed to:
- Quickly locate packed payloads, encrypted blobs, and shellcode
- Provide precise RVAs and VAs you can jump to immediately in:
- IDA
- Ghidra
- Reduce time wasted manually correlating entropy spikes with disassembly
The goal is shortening the distance between:
“This looks interesting” → “I’m reversing it.”
- Build the project using Visual Studio or your preferred IDE.
- Run
EntropyTool.exe. - Use the toolbar to select a PE file and scan its sections.
- Hover over the entropy graph to inspect individual blocks.
- Block size: Smaller blocks = finer resolution; larger blocks = smoother graph.
- All sections: Select “All Sections” at the top of the section list to visualize total entropy.
- Console output: Enable the console via the toolbar for debugging.
- Base ImGui integration inspired by adamhlt/ImGui-Standalone – thank you for providing a minimal ImGui foundation!
- Graphs made with epezent/implot - thank you for providing necessary libraries!
This project is licensed under the GPLv3 License – see LICENSE for details.