-
Notifications
You must be signed in to change notification settings - Fork 2
Fixed Arbitary Code Execution #1
base: master
Are you sure you want to change the base?
Conversation
|
👋 Hello, @jakevdp - @Anon-Artist has opened a PR to us with a fix for a potential vulnerability in your repository. To view the vulnerability, please refer to the bounty URL in the first comment, above. Ultimately, you get to decide if the fix is 👍 or 👎. If you are happy with the fix, please write a new comment ( If you have any questions or need support, come and join us on our community Discord! @jakevdp & @Anon-Artist - thank you for your efforts in securing the world’s open source code! 🎉 🔨 Want more security researchers protecting your repository? Stick our badge on your Copy this small code snippet and insert it into your
👇 👇 👇 |
|
Thanks - I deliberately used |
Thanks for your quick response @jakevdp but I think i can mention that in the era of secure coding most of the popular packages are moved on from FullLoader to SafeLoader. |
|
@jakevdp , @Anon-Artist , i think the fix isn't going to break any functionalities here , i think so , like at huntr similar fixes have been applied to microsoft repos like qlib lately. |
|
To be clear, in practice the exploit would look like this in a jupyter notebook cell: %%vegalite
!!python/object/new:type
args: ["z", !!python/tuple [], {"extend": !!python/name:exec }]
listitems: "__import__('os').system('xcalc')"After this fix, you could still accomplish the same thing by writing: import os
os.system('xcalc')Jupyter notebook already allows arbitrary code execution, so I'm not concerned about the yaml parser offering a backdoor to the same thing. |
|
OK
If this is intended then i think we can close this PR @JamieSlome
and thanks for your time
…On Tue, Feb 23, 2021, 3:43 AM Jake Vanderplas ***@***.***> wrote:
To be clear, in practice the exploit would look like this:
%%vegalite
!!python/object/new:type
args: ["z", !!python/tuple [], {"extend": !!python/name:exec }]
listitems: "__import__('os').system('xcalc')"
After this fix, you could still do the same thing with this:
import osos.system('xcalc')
Jupyter notebook already allows arbitrary code execution, so I'm not
concerned about the yaml parser offering a backdoor to the same thing.
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
<#1 (comment)>, or
unsubscribe
<https://github.com/notifications/unsubscribe-auth/AOV66JRS5JSXAPWASLRQQI3TALJI7ANCNFSM4YBF2TCA>
.
|
|
Hi @Anon-Artist @jakevdp , |
|
Thanks – I understand the potential attack mechanism here. I should have been more clear: the reason this is a non-issue is because the only context in which this code-path is used is for parsing the contents of a Jupyter code cell via a Jupyter cell magic; as such, arbitrary code execution is already possible by design. If this were used in another context, this patch would be correct, but the code is never used in any other context. |
|
oh ok @jakevdp thanks for the clearance . |

📊 Metadata *
Altairis a declarative statistical visualization library for Python. With Altair, you can spend more time understanding your data and its meaning. Altair's API is simple, friendly and consistent and built on top of the powerful Vega-Lite JSON specification. This elegant simplicity produces beautiful and effective visualizations with a minimal amount of code. Altair is developed by Jake Vanderplas and Brian Granger in close collaboration with the UW Interactive Data package is vulnerable toArbitrary Code Execution.Bounty URL: https://www.huntr.dev/bounties/1-pip-altair
⚙️ Description *
Vulnerable to YAML deserialization attack caused by unsafe loading.
💻 Technical Description *
Fixed by avoiding unsafe loader.
🐛 Proof of Concept (PoC) *
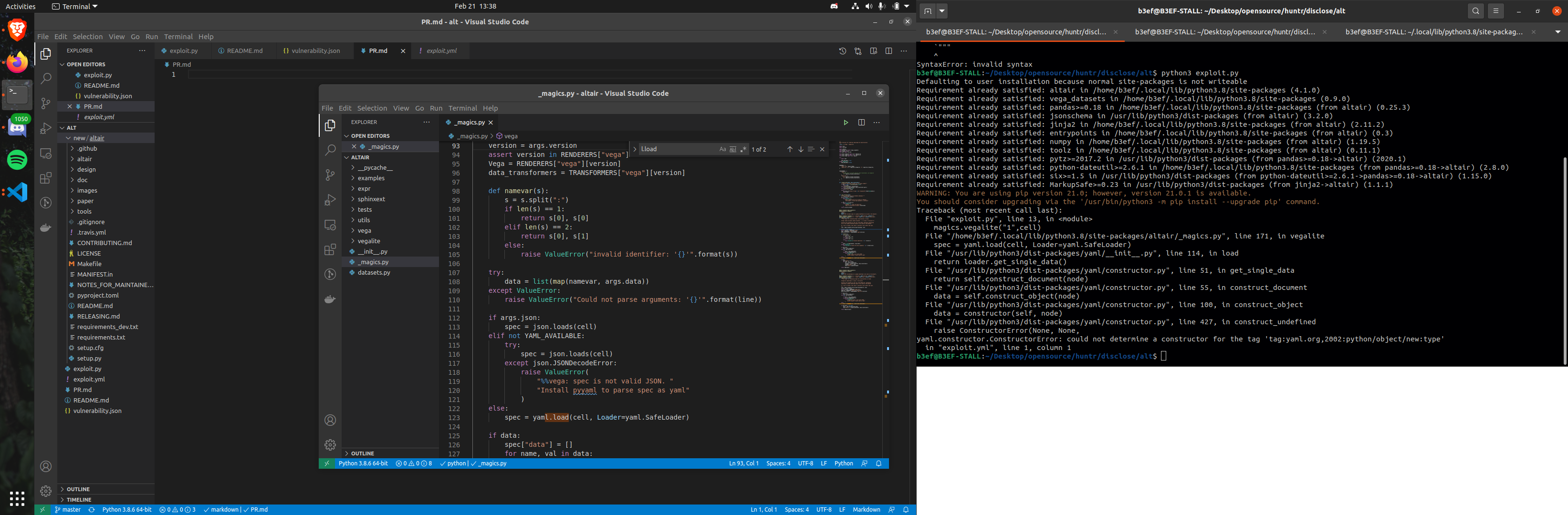
git clone http://github.com/vitessio/arewefastyetCreate the following PoC file:
exploit.yaml
Execute the commands in another terminal:
xcalc will pop up.
🔥 Proof of Fix (PoF) *
After fix Arbitary Code execution will never happen.
👍 User Acceptance Testing (UAT)
After fix functionality is unaffected.
🔗 Relates to...
https://www.huntr.dev/bounties/1-pip-altair