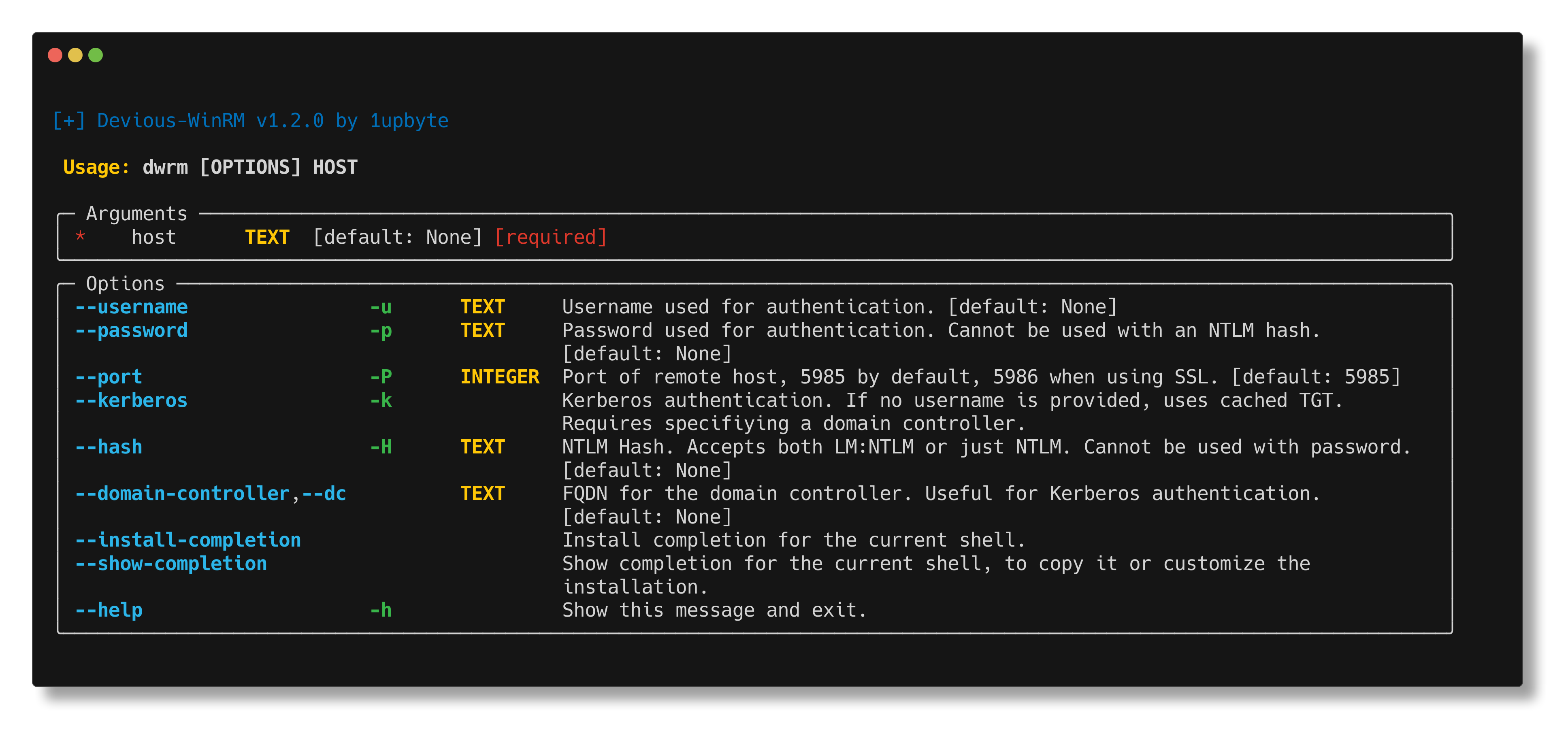
A Pentester's Powershell Client.
Devious-WinRM's initial reason for creation was due to how complicated Kerberos auth can be. With Devious-WinRM, on most operating systems, it is as simple as appending the -k flag to the command line. Devious-WinRM will automatically handle the rest.
Any .NET binary can be ran directly in the Powershell process' memory using the invoke command, usually bypassing AV detection. It's quick-and-easy way to covertly execute binaries without touching disk.
Some commands, such as Get-Service or qwinsta will fail to execute via WinRM due to a permission error. Devious-WinRM leverages RunasCs for an effortless way to get around this limitation of WinRM. Simply prepending the desired command with localexec will work.
Check out the Installation Guide for instructions.
TLDR: uv tool install devious-winrm
The Usage Guide has extensive documentation on every single feature and command.
- Evil-WinRM - This goes without saying, but Evil-WinRM is an incredible tool. It was the primary inspiration for this project.
- pypsrp - A tremendously well-featured library for Powershell Remote in Python. Super friendly developer as well!
- evil-winrm-py - Aditya and I had the same idea at almost the exact same time. I would be remissed if I didn't mention his project as well.
- RunasCs - Used for the local token upgrader. Super useful tool when doing work over WinRM.